Hiding files in a picture is actually quite easy and I thought it would be worth posting a little how-to for educational purposes. Once you know how easy it is, you will surely want to secure Windows 7 and check files for alternate data streams.
As mentioned in the intro, we are using alternate data streams to hide files in a picture. There are other ways to hide files in pictures, for example you could use the copy command to hide files in a pictures. Let’s take a look at that command first, before we try out alternate data streams.
Hide Files In A Picture via Copy /S
What do you need?
a) a picture
b) a zip files with your hidden files
Yup, it’s that easy.
1. Step Open a command prompt
2. Step Enter copy /b MyImage.jpg + Hidden.zip NewImage.jpg
3. Step Done! You have now merged the file MyImage.jpg and the Hidden.zip file to create a new file called NewImage.jpg. You have successfully hidden a file in a picture. Easy, huh? Simply replace the files names with your own files.
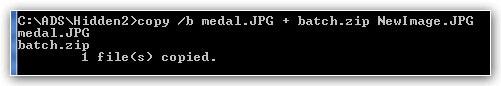
In this example I merged the image medal.jpg and the file batch.zip via copy /b medal.jpg + batch.zip NewImage.jpg. So, basically the image NewImage.jpg now includes the hidden zip file and whatever is in there.
Now, how to open the hidden file? Simply right-click on the image and open the image with your favorite zip program (7zip recommended) and you will be surprised to find a file inside it.
NTFS Alternate Data Streams: Critical Security Whole
The NTFS file system that most modern Windows PC’s use provide a feature called alternate data streams. It might be the biggest security flaw of NTFS and is being abused by many hackers. An ADS can not only hide files in a picture, it can also hide processes, making it almost impossible to detect malicious processes hidden in a file. Process managers like the Windows Task Manager can not detect the execution of a hidden process, making alternate data streams a really critical security whole!
Hiding Files In Alternate Data Stream of a Picture
What we are going to do now is only for educational purposes, please do not abuse this knowledge. I want to show everyone how easy it is to abuse NTFS and what you can do about it!
1. Step Create a new folder where you create your picture and the hidden file, I called it ADS
2. Step CD to this folder, e.g. enter CD C:\ADS\
Next, we are going to hide the file batch.bat in the JPG image medal-of-honor-beta-client.jpg.
3. Step Enter C:\ADS\>echo “ADS” > medal-of-honor-beta-client.jpg:batch.bat
4. Step That it’s! Now you added the batch file to the alternate data stream of the JPG image. The batch is hidden inside the picture. Simply replace the image name with your own image. The batch file can be any file, even an executable.
5. Step Let’s check the directory! Enter dir to get a list of all files in the directory:
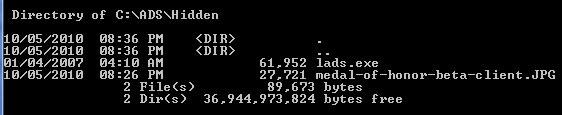
As you can see there’s only the .exe file lads.exe (more about it later) and the JPG image, nothing else.Where is the the hidden batch file? It’s hidden inside the picture.
Detect Alternate Data Streams
6. Step Next, it would be interesting to detect the alternate data stream, don’t you think?
Download Lads from heysoft.de
7. Step Copy lads.exe and your image with the hidden file inside to a new folder, then simply enter lads to scan the directory for files with hidden data streams.
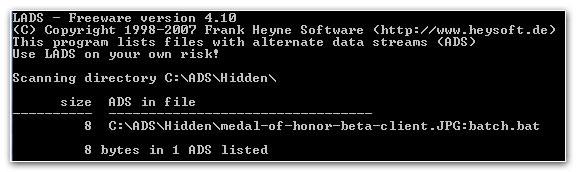
8. StepLads found the alternate data stream and will list the affected files.
Delete Alternate Data Streams
Ok, now we know there is a potentially harmful file! Let’s delete the alternate data stream!
9. Step Download Streams from Sysinternals
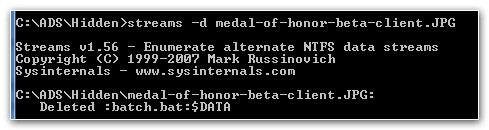
10. Step Copy streams.exe into the folder with the file that has alternate data streams.
11. Enter streams -d filename.exe
12. Streams will then delete the alternate data streams!
Now you know how to hide files within a picture, you know how to create alternate data streams, how to detect alternate data streams and how to delete alternate data streams. Looks like we’ve learned quite a lot here. So, next time you copy a suspicious file make sure to run lads to scan for alternate data streams!